Human Error: The Most Overlooked Cybersecurity Threat in 2025
Why Human Error Remains a Critical Vulnerability?
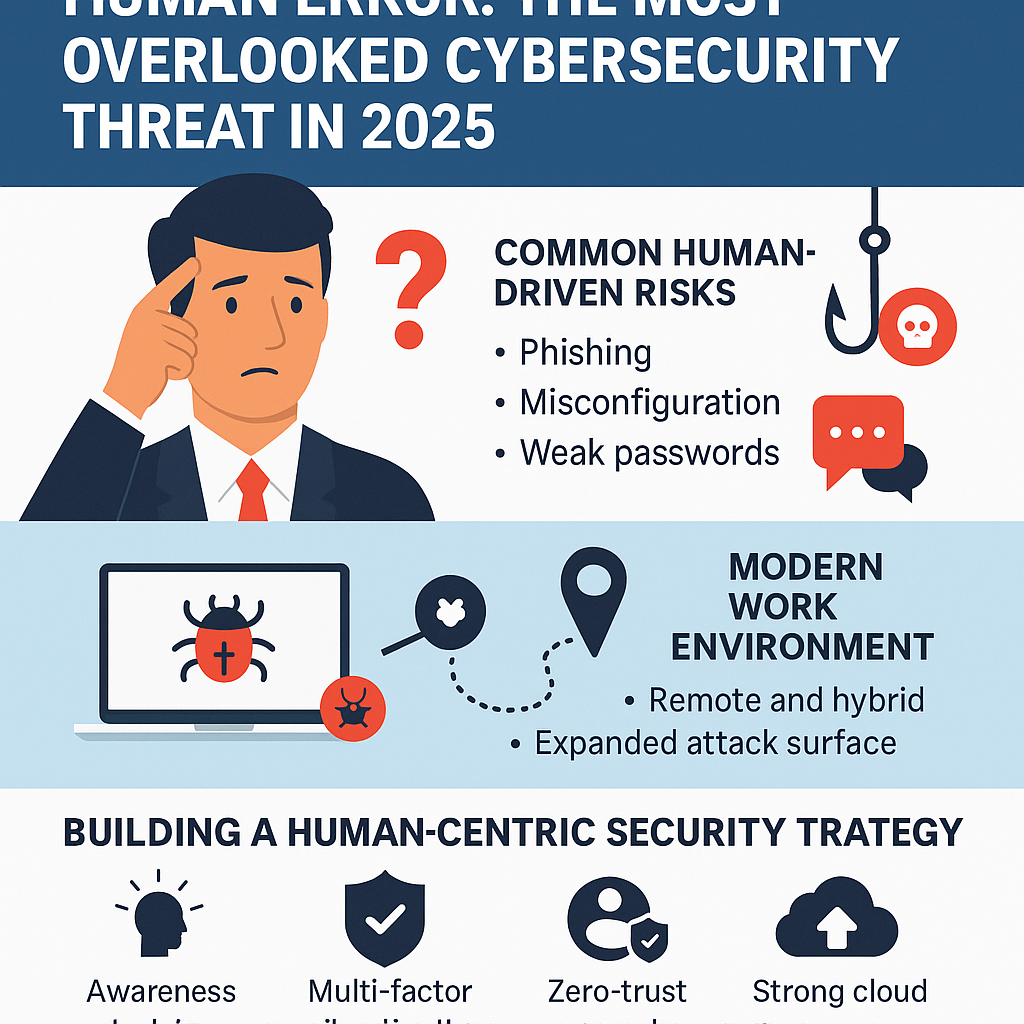
Attackers understand that while technology evolves, human behavior is slower to change. They increasingly rely on psychological manipulation—leveraging urgency, fear, curiosity, and trust.
Common human-driven security failures include:
>Reusing passwords across multiple platforms
>Falling for well-crafted phishing or smishing messages
>Misconfiguring cloud services, leaving databases public
>Ignoring security updates or bypassing MFA prompts
>Sharing sensitive information over unsecured channels
Remote and hybrid work models have expanded the attack surface. Employees now access sensitive systems from personal devices, home networks, and unmanaged environments.
This leads to:
>Inconsistent security hygiene
>Weaker network visibility
>Higher dependency on user vigilance
>More opportunities for credential theft
Building a Human-Centric Security Strategy
Organizations must now treat users as both a potential vulnerability and a critical line of defense. Key steps include:
1. Continuous Awareness Training
One-time training doesn’t work. Cyber threats evolve, and so must employee education—monthly simulations, micro-learning modules, and scenario-based exercises are essential.
2. Multi-Factor Authentication Everywhere
MFA dramatically reduces account takeover risks, even if credentials are compromised.
3. Zero-Trust Access Controls
No user—internal or external—should have implicit trust. Access must be strictly verified, limited, and monitored.
4. Automated Safety Nets
Implement AI-driven email filtering, passwordless authentication, behavioral analytics, and automated alerting to reduce reliance on human judgment alone.
5. Strong Cloud Governance
Standardized templates, guardrails, and automated misconfiguration detection prevent human mistakes from becoming national-security-level vulnerabilities.
❤ 3 · 💬 3
Want to like or comment? Sign in or create an account.